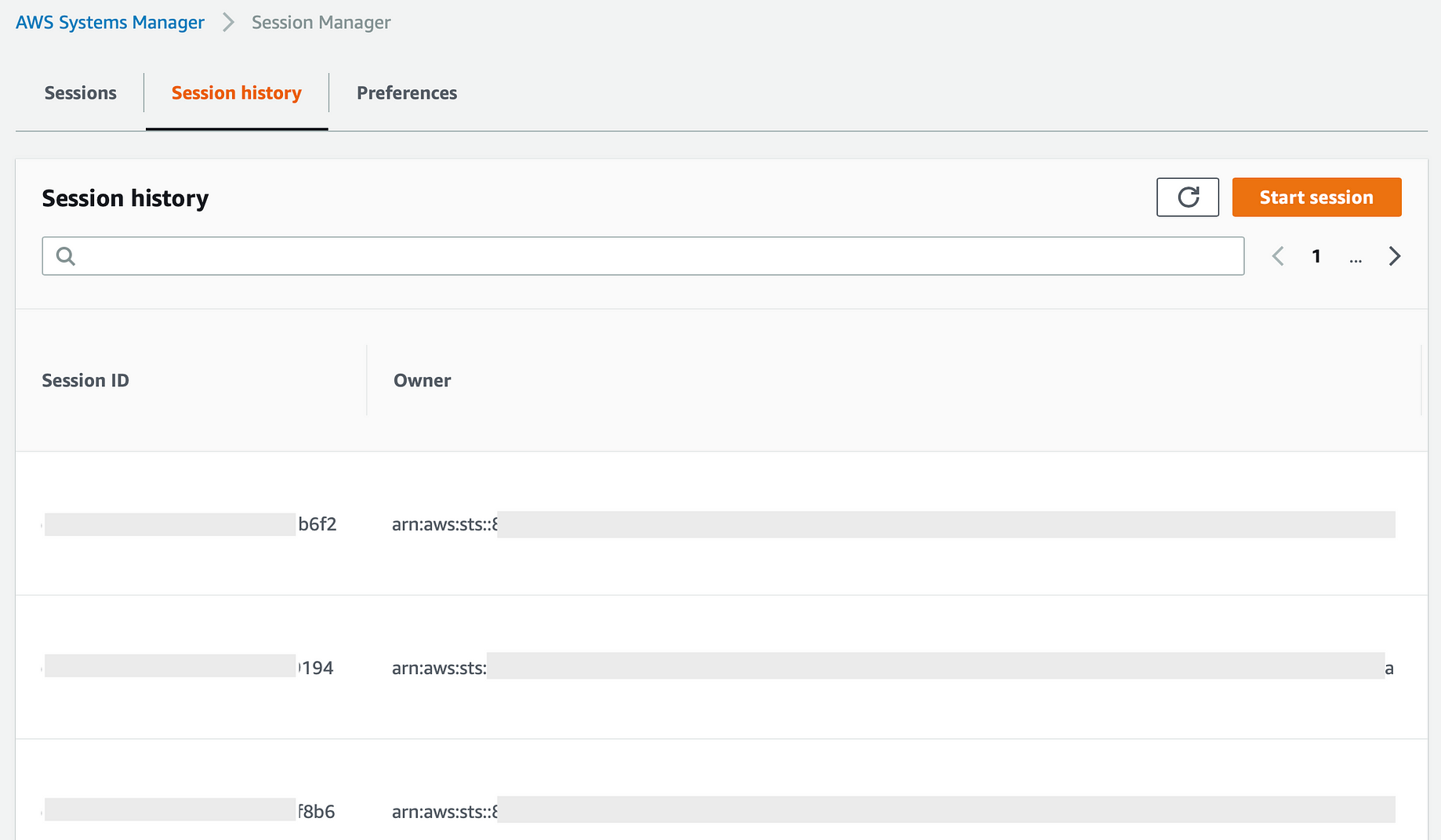
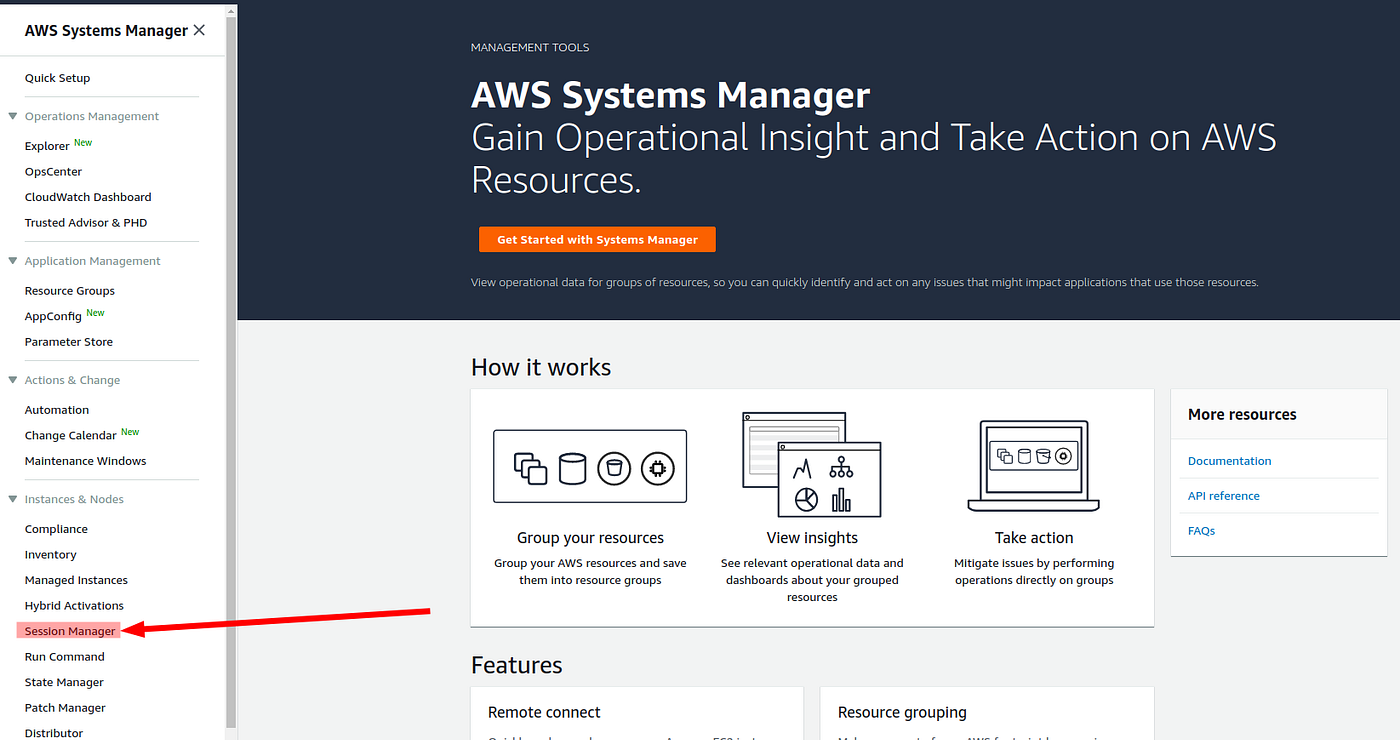
How To Add An EC2 Instance To AWS System Manager (SSM) Hello Everyone Welcome to CloudAffaire and this is Debjeet In the last blog post, we have discussed how to install AWS System Manager (SSM) Amazon Redshift launches RA3 in Hong Kong and China Regions (Beijing, Ningxia) AWS Elemental MediaPackage extends its metadata passthrough capabilities ;Let's have a look at how it is on a less theoretical level Ok, so you have created an ifafafafafafafa AWS instance in your private subnet but for some reason, you need an SSH like connection to it to maybe use it hopefully not too often In the old days, having a bastion host used to be an acceptable choice On these days, not so much Basically

Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh
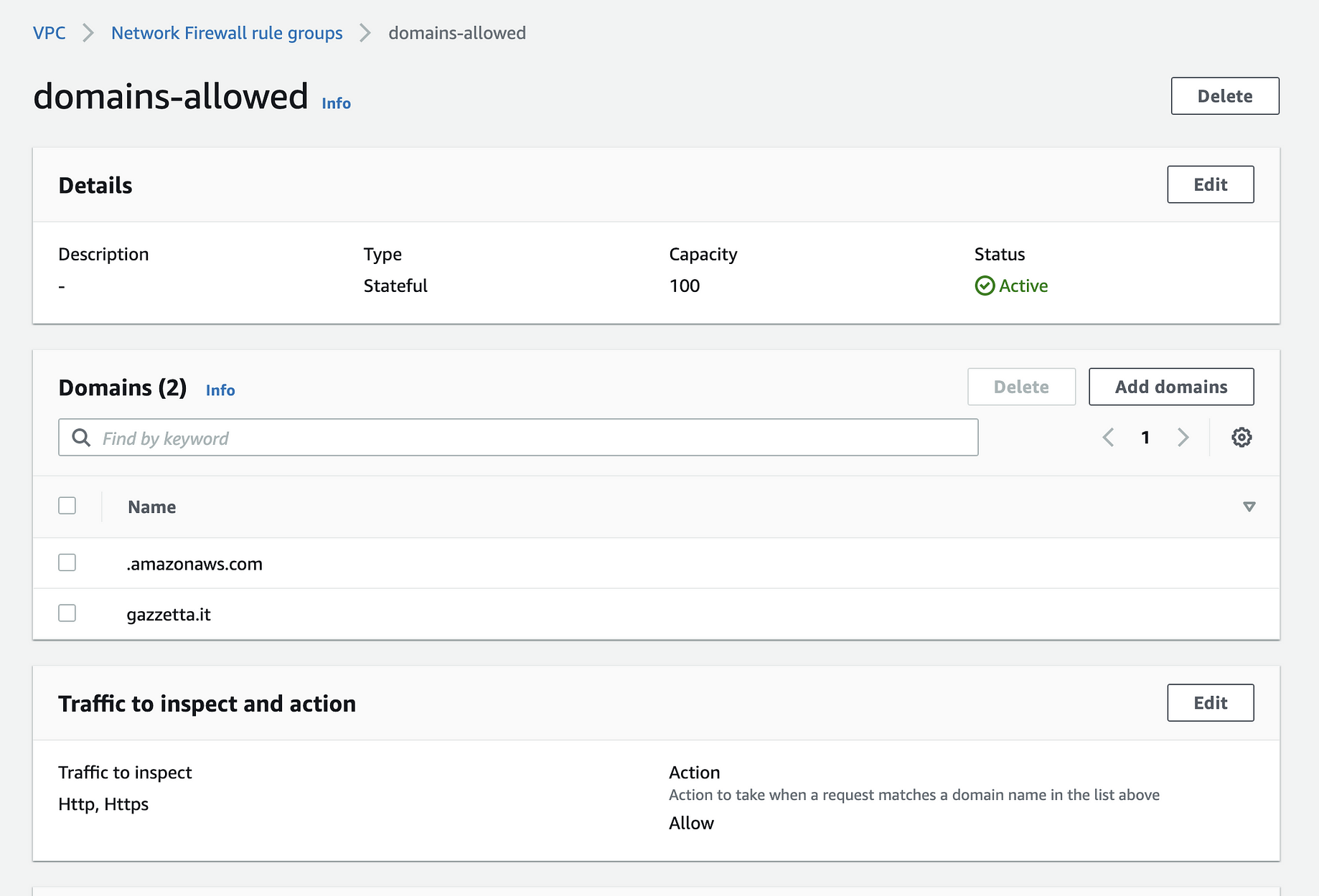
Amazonssmmanagedinstancecore terraform
Amazonssmmanagedinstancecore terraform- Similarly, in the worker role, we are permitting EC2 instances to assume roles and then attaching the managed policies AmazonEKSWorkerNodePolicy, AmazonEC2ContainerRegistryReadOnly, and AmazonSSMManagedInstanceCore to the worker role To execute the IAM script run below commands terraform plan terraform apply autoTerraform validate can also be run using the setting in the command palette Release History v0 is the first official release from HashiCorp, prior releases were by Mikael Olenfalk The 0 release integrates a new Language Server package from HashiCorp The extension will install and upgrade terraformls to continue to add new




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh
Did you get excited about this article?The default value is 24 hours from resource creation time Terraform will only perform drift detection of its value when present in a configuration iam_role (Required) The IAM Role to attach to the managed instance registration_limit (Optional) The maximum number of managed instances you want to register The default value is 1 instanceAWS Glue Studio now provides data previews during visual job authoring
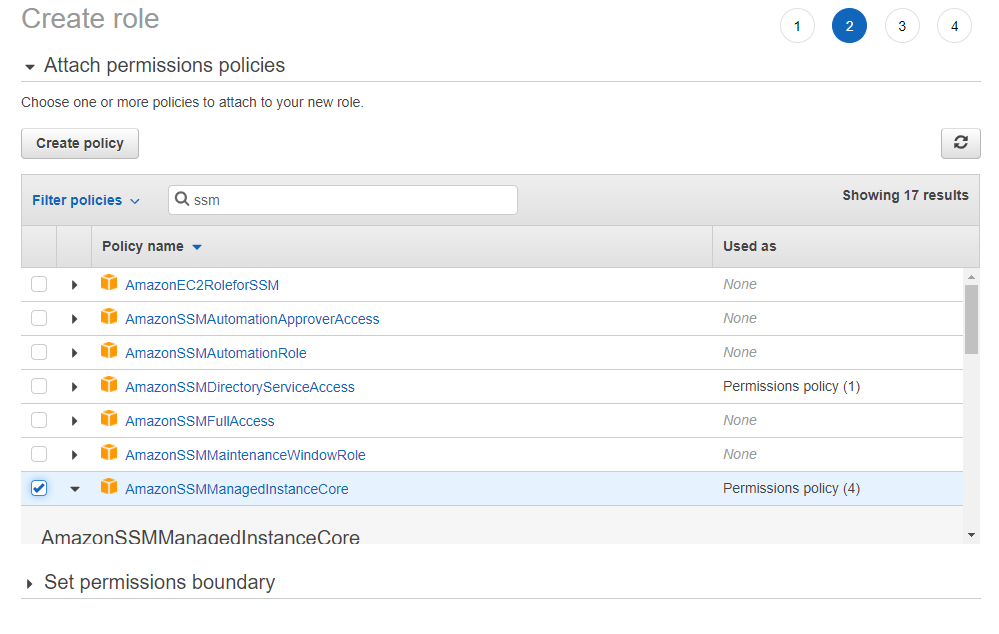
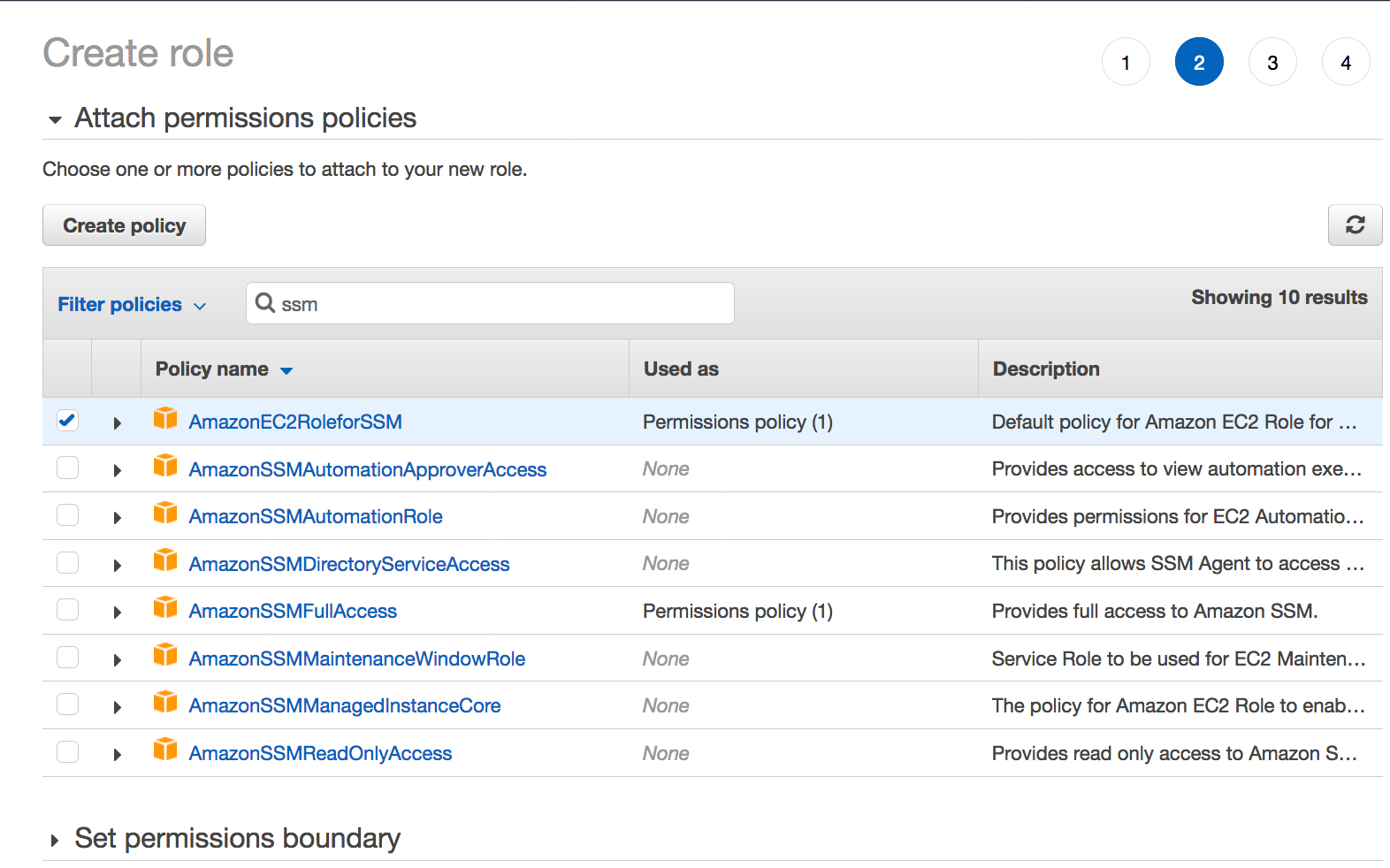
SSM SessionManagerでのコンソールの操作ログをS3やCloudWatchLogsに保存できるということなので試してみた。Terraformで設定。 1 IAMrole / Instance Profileを作成 ec2インスタンスにインストールされているSSMエージェントがログを書き込むので、インスタンスに権限を付与してあげる必要がある。こちらのYou may now begin working with Terraform Try running "terraform plan" to see any changes that are required for your infrastructure All Terraform commands should now work If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directoryThe first policy, AmazonSSMManagedInstanceCore, enables an instance to use AWS Systems Manager service core functionality Depending on your operations plan, you might need permissions represented in one or more of the other three policies
Nginx CloudWatch Agent GitHub Gist instantly share code, notes, and snippetsAzure Monitor Dashboard To achieve this we used Terraform, Chef, PowerShell scripts and ARM templates to build Azure Monitor to fit our requirements The basic structure for Azure Monitor in this scenario is as follows Create Azure storage account for monitoring, Azure Application Insights, Log Analytics Workspace and monitor action groupFor use with my newly created ECS Cluster I also added two EC2 instances into my Terraform script They are placed in public subnets so they have direct access to the internet More important than internet access is that they have to have proper IAM permissions in their IAM role since the SSM agent will be installed and used for registration in




Amazon Ec2 Noise Page 3




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh
自分で作成したIAMpoliciesであれば、datasource利用してPolicy document作成し、aws_iam_role_policy_attachmentで紐づければ良いけど、AWS managedの場合どうするのがよいか調べたのでメモ。 方法1 直接ARNを書く 例えば AmazonSSMMan2 コード Terraformのコードが長いので、スッキリさせるために折り畳んで表記しています。 コードを展開したい場合は、各項目の「 ︎」をクリックしてください。 ・VPC関連Background This branch adds support for AWS SSM, as well as adding other arbitrary IAM roles to the IAM instance profile SSM provides a more secure alternative to the bastion host approach for establishing connections to private network infrastructure This branch also replaces the contents of the networking submodule with a dependency on the community terraformawsvpc module
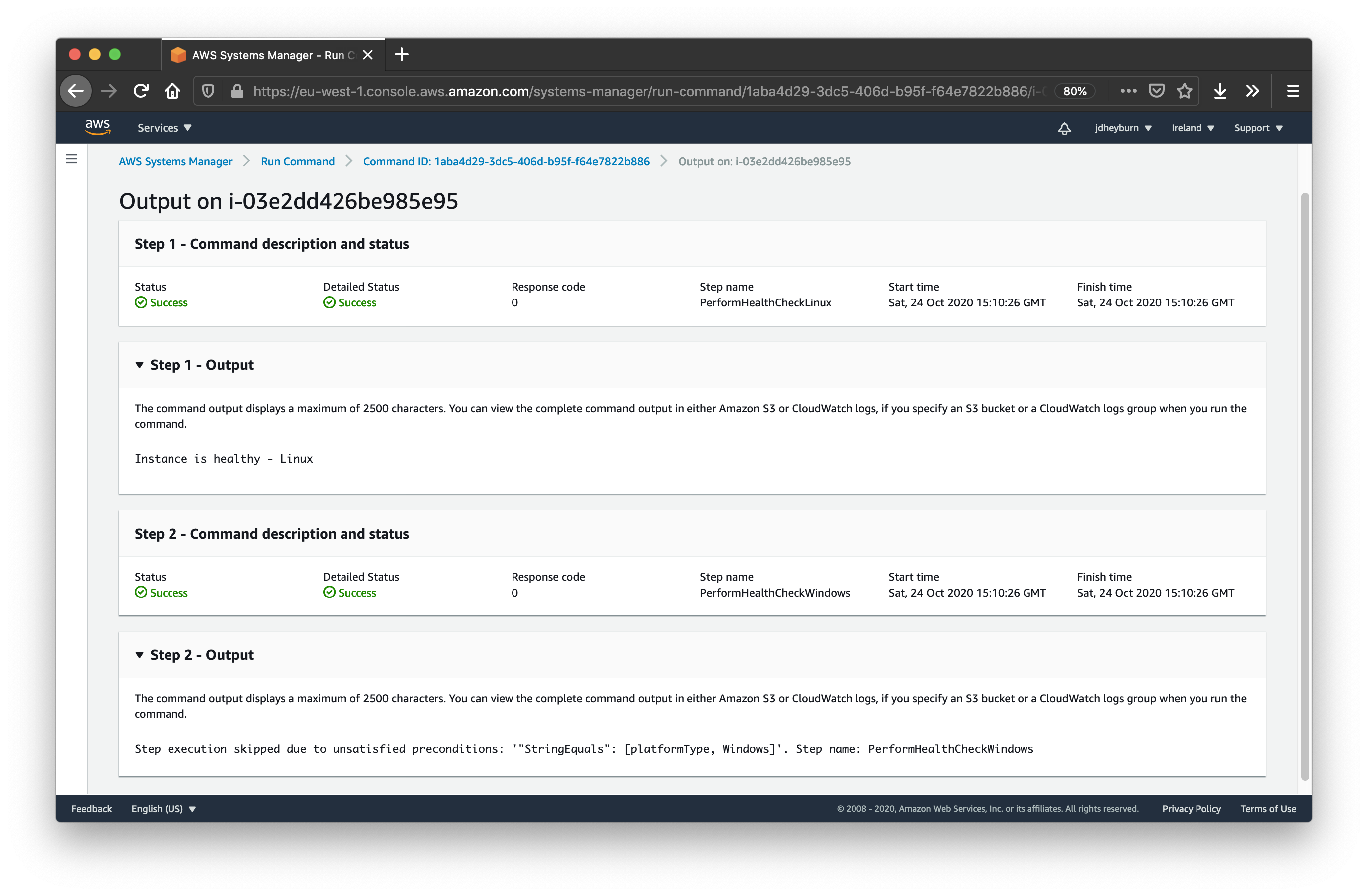



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn
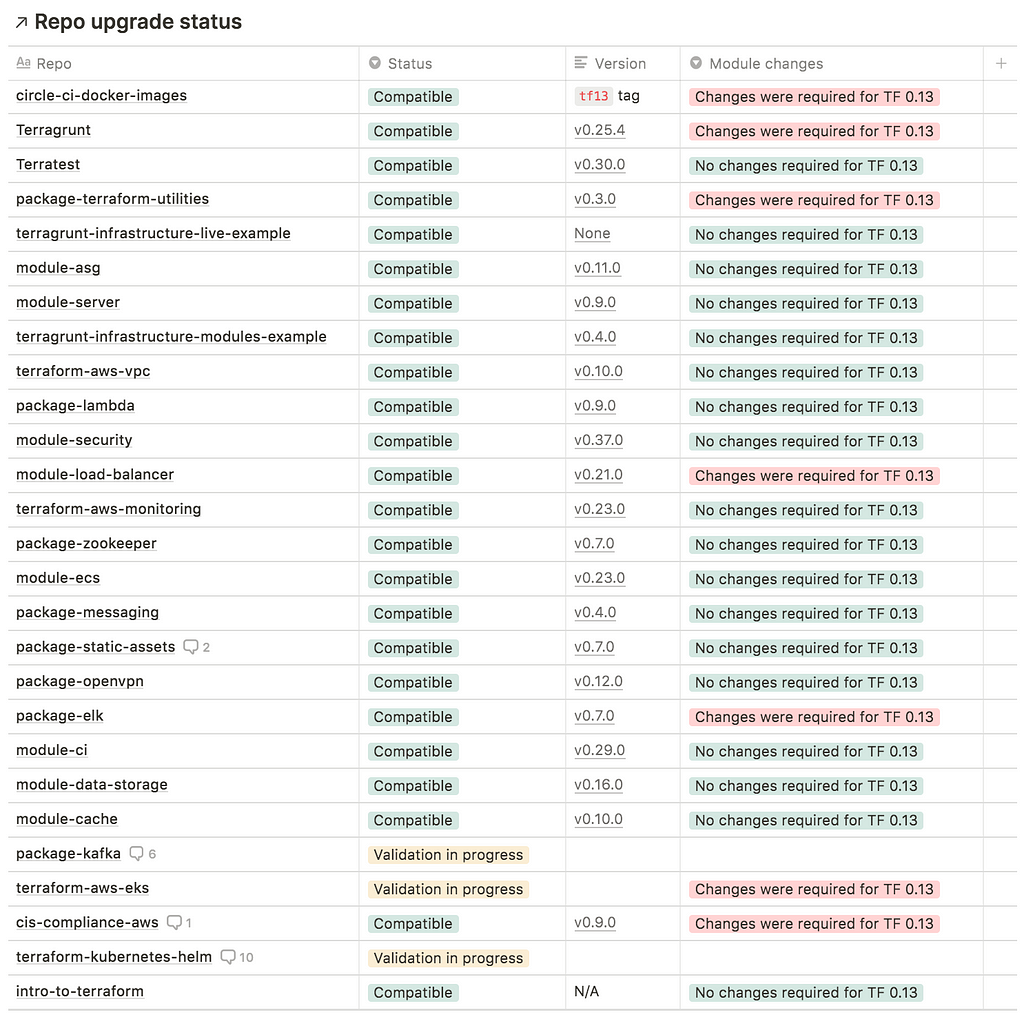



Gruntwork Newsletter November Laptrinhx
This past December I gave a talk at the SoCal PowerShell User Group about using the AWSPowerShell module to work with AWS and deploy an IIS web server into a VPC that is configured with AWS Systems Manager and PowerShell DSC If you watched the recording or attended, you will remember that the scope of the presentation was large With this blog post, ITerraform Registry aws provider Guides ACM ACM PCA API Gateway (REST APIs) API Gateway v2 (WebSocket and HTTP APIs) Access Analyzer Amazon Managed Service for Prometheus (AMP)Terraform allows infrastructure to be expressed as code in a simple, human readable language called HCL (HashiCorp Configuration Language) It reads configuration files and provides an execution plan of changes, which can be reviewed for safety and then applied and provisioned
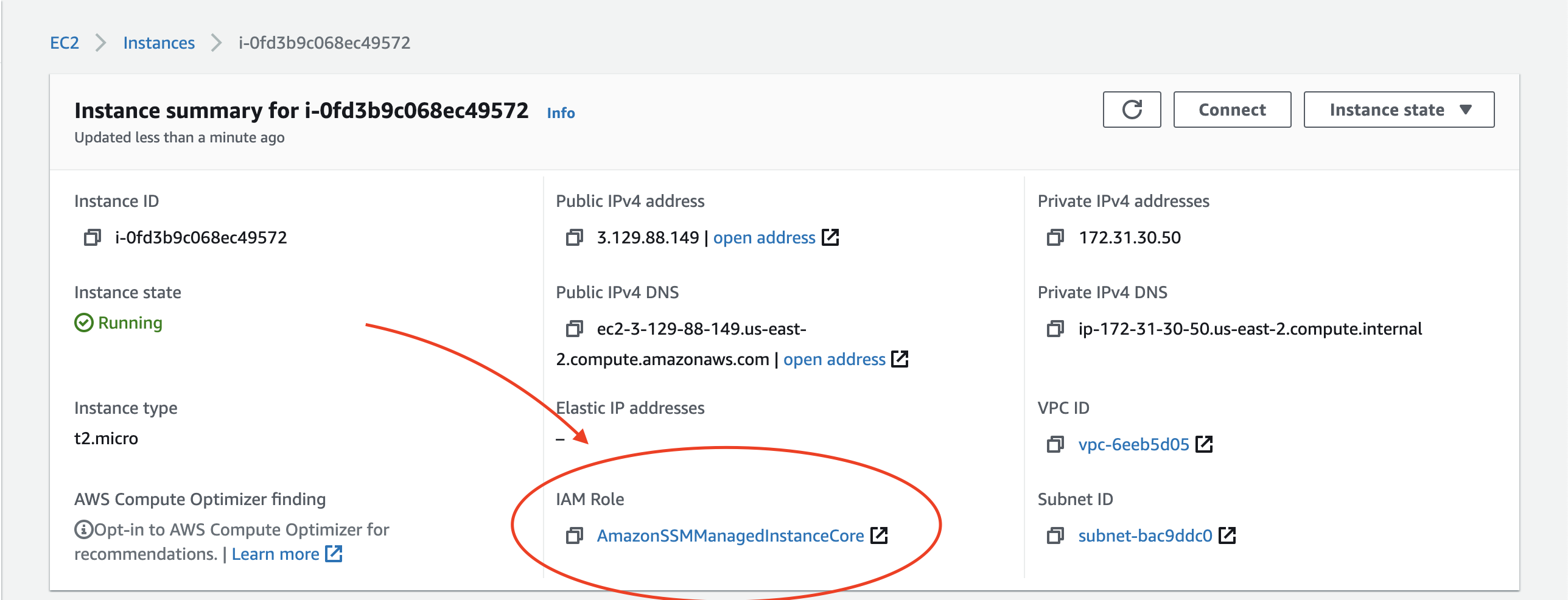



Adding An Ec2 Instance



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium
The Terraform Associate certification is for Cloud Engineers specializing in operations, IT, or development who know the basic concepts and skills associated with open source HashiCorp Terraform Terraform Module POC for AWS Network Firewall I created this module in Terraform so you can do the test as well and also you can start from there and customize it for your environment I publish the code on the terraform registry on this page To run in your environment you can do it like that and in few minutes you can have a working POCTerraform has been successfully initialized!



Qs R5elsxyhm M
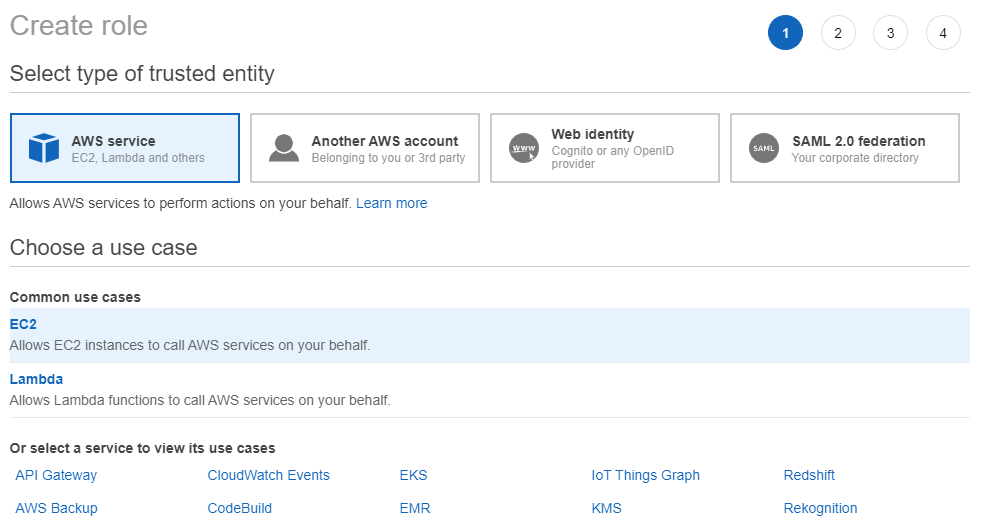



Automate Patching With Aws Systems Manager By Troy Ingram Nerd For Tech Medium
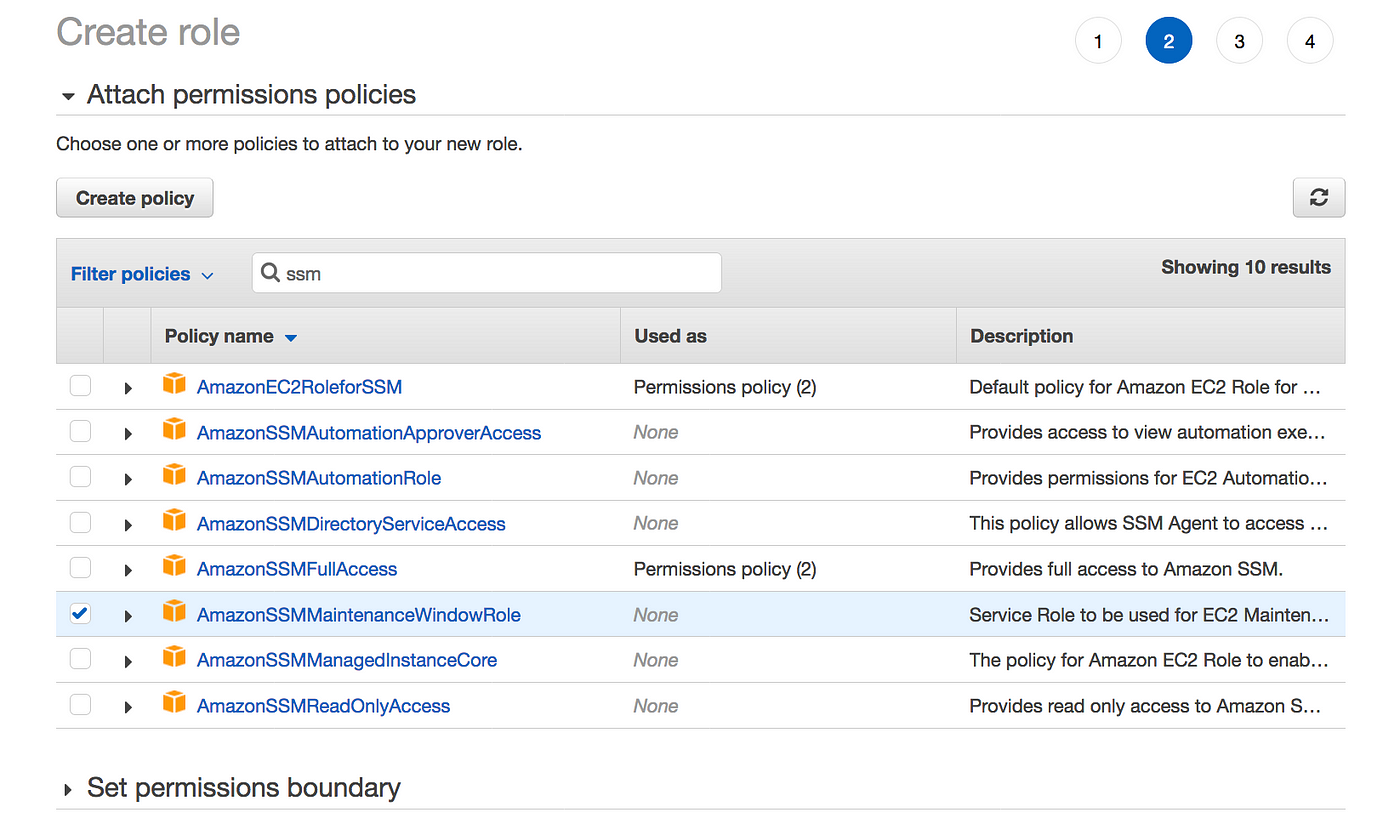
To make APIs calls to a Systems Manager endpoint, you must attach the AmazonSSMManagedInstanceCore permissions policy to the IAM role attached to your instance If you're using a custom IAM policy, confirm that your custom policy uses the permissions found under AmazonSSMManagedInstanceCore Also, make sure that the trust policy of the IAM role Hashicorp Terraform is an opensource tool for provisioning and managing cloud infrastructure It codifies infrastructure in configuration files that describe the topology of cloud resources These resources include virtual machines, storage accounts, and networking interfaces The Terraform CLI provides a simple mechanism to deploy and versionInstall EC2 instance connect on the bastion or update my AMI I found that EC2 instance connect comes preinstalled with certain




Install Agent On Aws Ec2 Instances Using Terraform And Aws Systems Manager Lacework



Add Ssm Session Manager Support Issue 121 Npalm Terraform Aws Gitlab Runner Github
Additionally it will create one security group and one IAM role with the AmazonSSMManagedInstanceCore policy attached to the IAM role for the instance Have a look into maintf Note that this module is written for terraform client ver 014 or later Use release earlier releases for prior terraform versionsTerraform on Azure documentation Learn how to use Terraform to reliably provision virtual machines and other infrastructure on AzureThis Product Guide provides a detailed look at how Rackspace delivers our Fanatical Support for AWS offering It covers core concepts such as the AWS account structure, Rackspace service levels and advanced concepts such as providing access requests to instances via Rackspace Passport and accessing audit logs via Rackspace Logbook



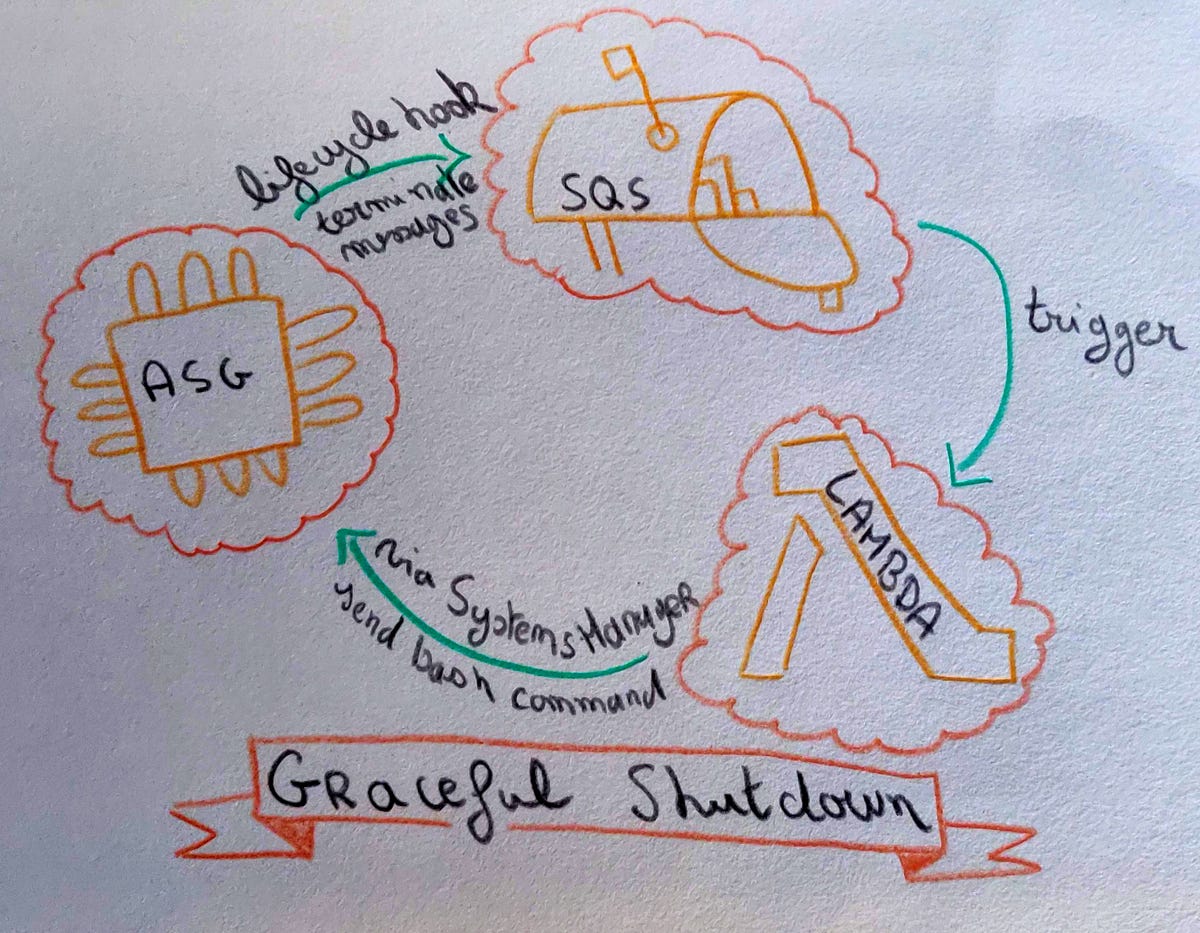
Graceful Shutdown Using Simple Sytems Manager And Terraform On Aws By Paul Leclercq Tabmo Labs




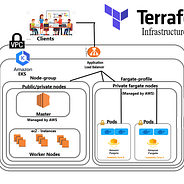
Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers
#terraform #terraformtutorial #infrastructureascodeTerraform is an opensource tool that enables you to automate and manage your infrastructure, platform, an How To Execute A Command Using AWS SSM Run Command Hello Everyone Welcome to CloudAffaire and this is Debjeet In the last blog post, we have discussed AWS SSM documents and how to create one This is usually not an issue as most offical AMI on AWS already have it setup Instance role with AmazonSSMManagedInstanceCore AWS managed policy Since runcommand is not supported by terraform, you either have to use localexec to run the command through AWS CLI, or through lambda function using aws_lambda_invocation



Infosanity Blog Offensive And Defensive It Security




Install Agent On Aws Ec2 Instances Using Terraform And Aws Systems Manager Lacework
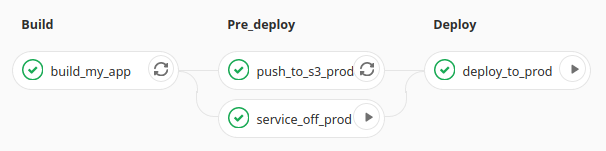
Automate all the things At TabMo, we slowly but surely move our services from Jenkins to GitlabCI and automate all the things that can be thanks to blue/green deployments with Terraform or docker images for integration testsOur goal is to reduce human checks, or SSH connections as much as possible We encounter a problem for slowterminating app such asEC2생성 키페어 생성 먼저 인스턴스에 사용할 키 페어를 생성합니다 기존에 사용하던 키가 AWS 상에 등록되어 있다면Get Started AWS 40 min 8 tutorials Build, change, and destroy AWS infrastructure using Terraform Stepbystep, commandline tutorials will walk you through the Terraform




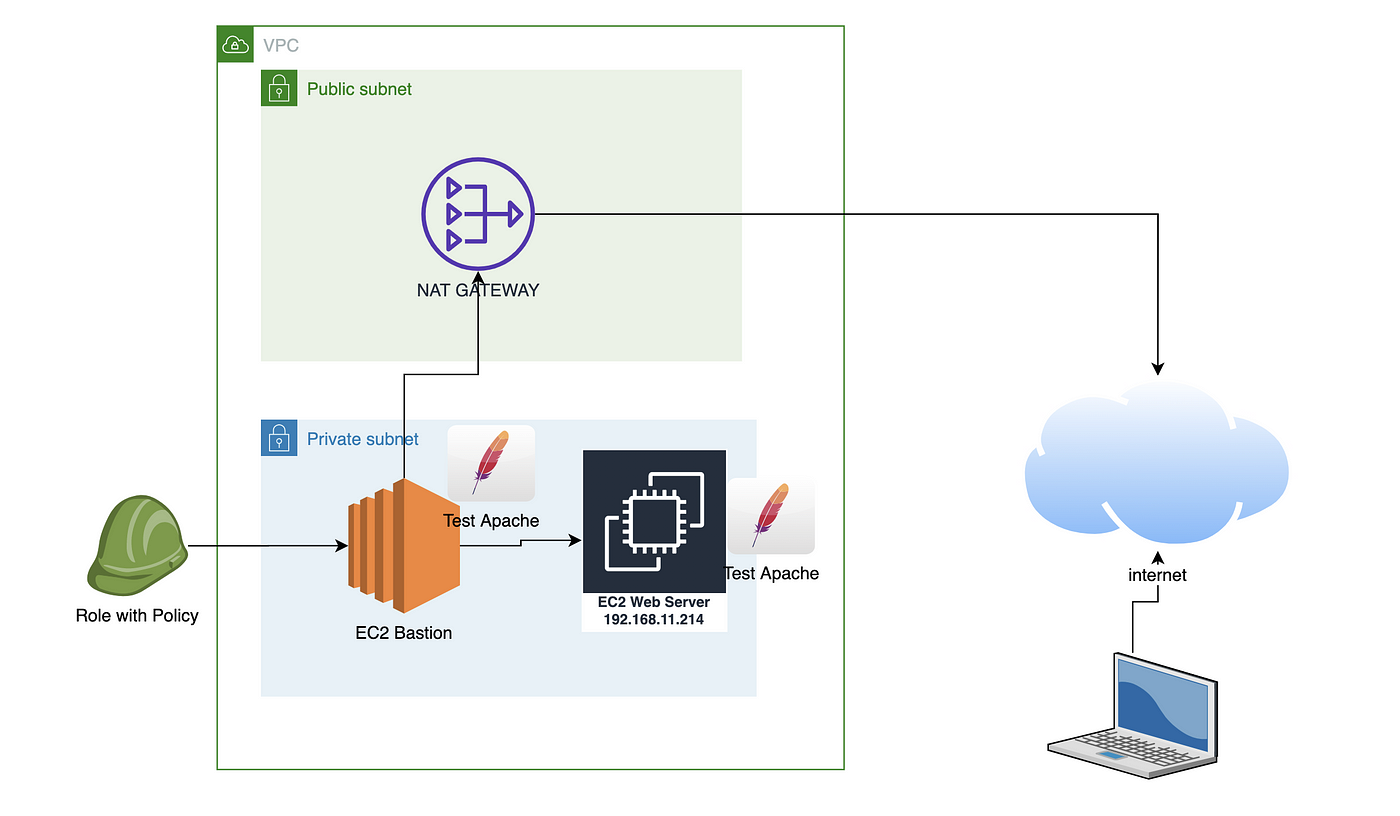
Login From Internet Into A Private Subnet With Session Manager By Giuseppe Borgese Medium




Tf Destroy Fails To Remove Aws Auth Unauthorized Issue 1162 Terraform Aws Modules Terraform Aws Eks Github
Amazon EKS managed node groups now supports parallel node upgrades ; You can use the AWSprovided AmazonSSMManagedInstanceCore Managed Policy for this, or craft your own policy Kicking the tires If you want a quick way to try Session Manager out, the terraformoktassmmodules repo has examples to get you started Further reading Disney Streaming released SSM Helpers, How I set up secure AWS RDS access using SSM and EC2 instance profile with terraform How I set up secure AWS RDS access using SSM and EC2 instance profile with terraform policy/AmazonSSMManagedInstanceCore;




Terraform Aws Ec2 With Ssm Agent Installed



Not Possible To Upgrade To Terraform 0 12 If Using Resource Aws Lb Listener Certificate Terraform Provider Aws
CloudFormation, Terraform, and AWS CLI Templates Configuration to create an IAM role for EC2 instances to access to AWS Systems Manager (SSM) services, with the least permissions required Terraform does not yet have native support for decrypting files in the format used by sopsOne solution is to install and use the custom provider for sops, terraformprovidersopsAnother option, which I'll demonstrate here, is to use Terragrunt, which has native sops support built in Terragrunt is a thin wrapper for Terraform that helps you keep your TerraformI'm trying to call an SSM document using terraform to stop an ec2 instance But, it doesn't seems to work I keep having the error Automation Step Execution fails when it is changing the state of each instance Get Exception from StopInstances API of ec2 Service



Github Notarize Terraform Aws Ec2 Asg



Tf Destroy Fails To Remove Aws Auth Unauthorized Issue 1162 Terraform Aws Modules Terraform Aws Eks Github
구성도 VPC x 1 (작성 완료) IAM(Role AmazonSSMManagedInstanceCore) x 1;Access to AWS resources requires permissions You can create IAM roles and users that include the permissions that you need for the CloudWatch agent to write metrics to CloudWatch and for the CloudWatch agent to communicate with Amazon EC2 and AWS Systems Manager Terraform을 이용하여 관련 Resource들을 AWS에 배포 Role에 AmazonSSMManagedInstanceCore라는 Policy를 추가하였는데, 이건 Session Manager를 이용해서 EC2에 접속하기 위함이다 이 Policy를 제외하고 SSH Terminal을 통해서 접속하거나 EC2 Instance Connect (browserbased SSH connection)로 접속을




Terraform Aws Elastic Beanstalk Environment




Install Agent On Aws Ec2 Instances Using Terraform And Aws Systems Manager Lacework
Dynamic IAM Resources with Terraform IAM requirements differ between project to project Depending on the complexity, we could create the IAM resources with Terraform in the relevant layer However, having the IAM resources dynamically create within its own module, or even combining them with their resource counterparts, gives us great powerTerraform is distributed as a single binary Install Terraform by unzipping it and moving it to a directory included in your system's PATH You can find the SH56 checksums for Terraform 101 online and you can verify the checksums signature fileInstall Terraform on Mac, Linux, or Windows by downloading the binary or using a package manager (Homebrew or Chocolatey) Then create a Docker container locally by following a quickstart tutorial to check that Terraform installed correctly




Gruntwork Newsletter November By Amanda Ohmer Gruntwork




How To Add An Ec2 Instance To Aws System Manager Ssm Cloudaffaire
I was wondering if anyone could help with this issue?After the outputs of running terraform init and terraform plan out plan look good, run a terraform apply to create the resources Once completed, we're ready to ssh onto the instance!Establishing SSH Tunnel To begin, run the command ssh L 5432`terraform output raw rds_endpoint` Nf ubuntu@`terraform output raw bastion_ip`
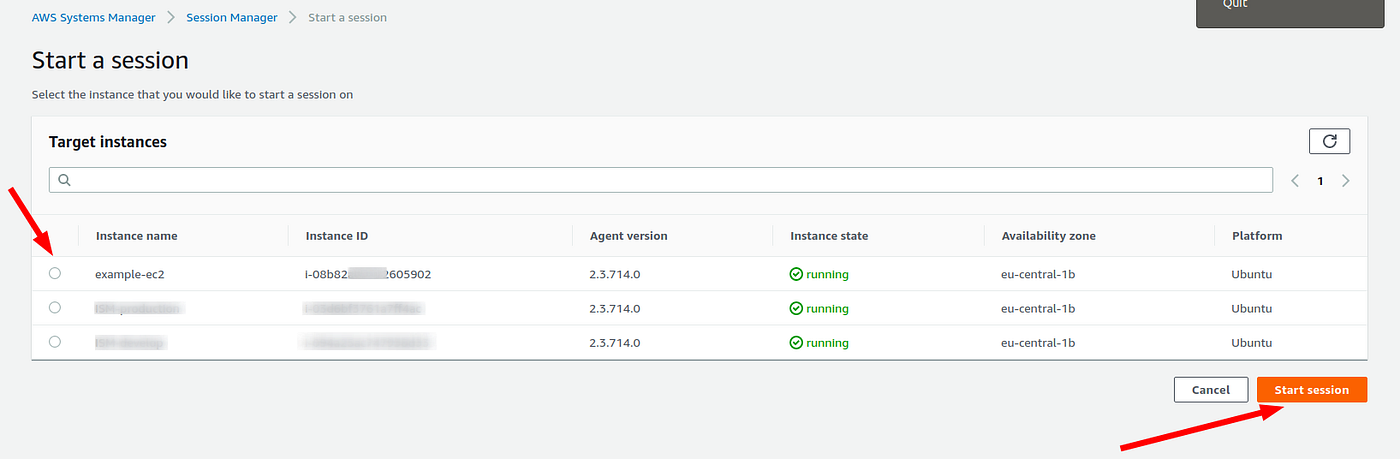



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium




Aws Session Manager Less Infrastructure More Features Sym Blog
🔥Intellipaat AWS training course https//intellipaatcom/awscertificationtrainingonline/In this aws terraform tutorial for beginners video you will lear



Graceful Shutdown Using Simple Sytems Manager And Terraform On Aws By Paul Leclercq Tabmo Labs




Stop Exposing Port 22 To The World It S Time To Rework Your Remote Access Methods Toolr Io




Secure Rds Access Through Ssh Tunneling Over Aws Ssm In Terraform



Sweetops Terraform For November




Amazon Ec2 Noise Page 3




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh




Building Amis Packer And Image Builder




How To Add An Ec2 Instance To Aws System Manager Ssm Cloudaffaire



Docs Aws Amazon Com Systems Manager Latest Userguide Systems Manager Ug Pdf




Terraform Multi Cloud Demo Part 3 Aws Infrastructure Dave S Blog




Launching Ec2 Using Ssm With Prod Uatprivileges Aws



Aws Iam Policy Attachment Error When Attaching Amazon Managed Policies Issue 5979 Hashicorp Terraform Github




Terraform Aws Modules Iam Aws Terraform Registry
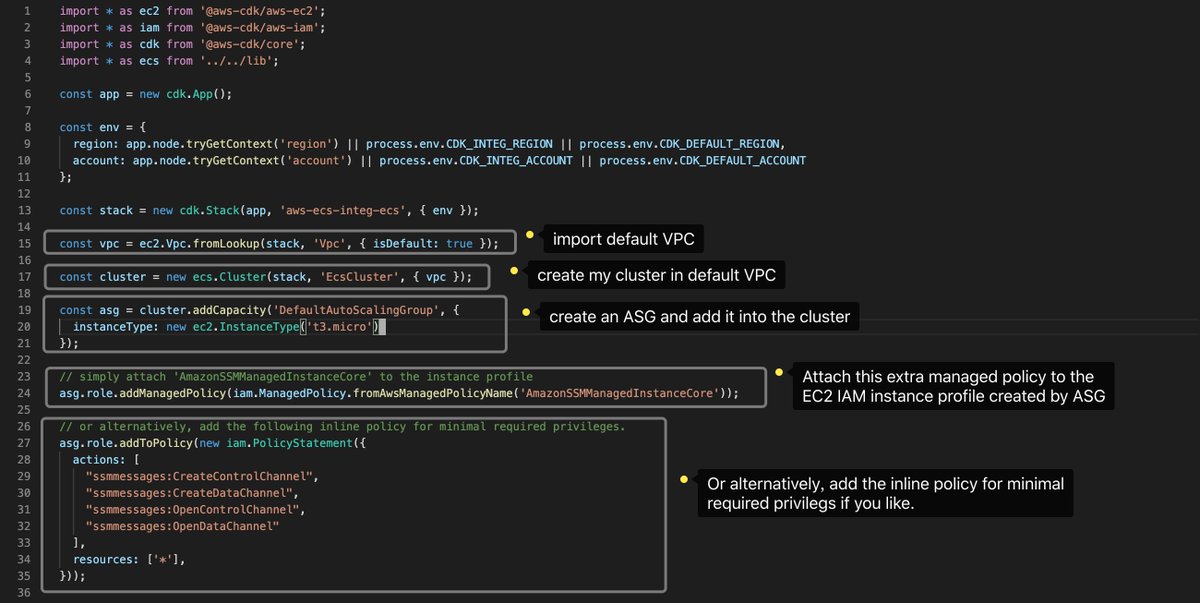



Pahudnet The Interesting Thing Is That I Can Just Write 2 Or 3 Awscdk Statements Like This To Bring Up My Amazon Ecs Cluster With Latest Amazon Ecs Optimized Linux 2
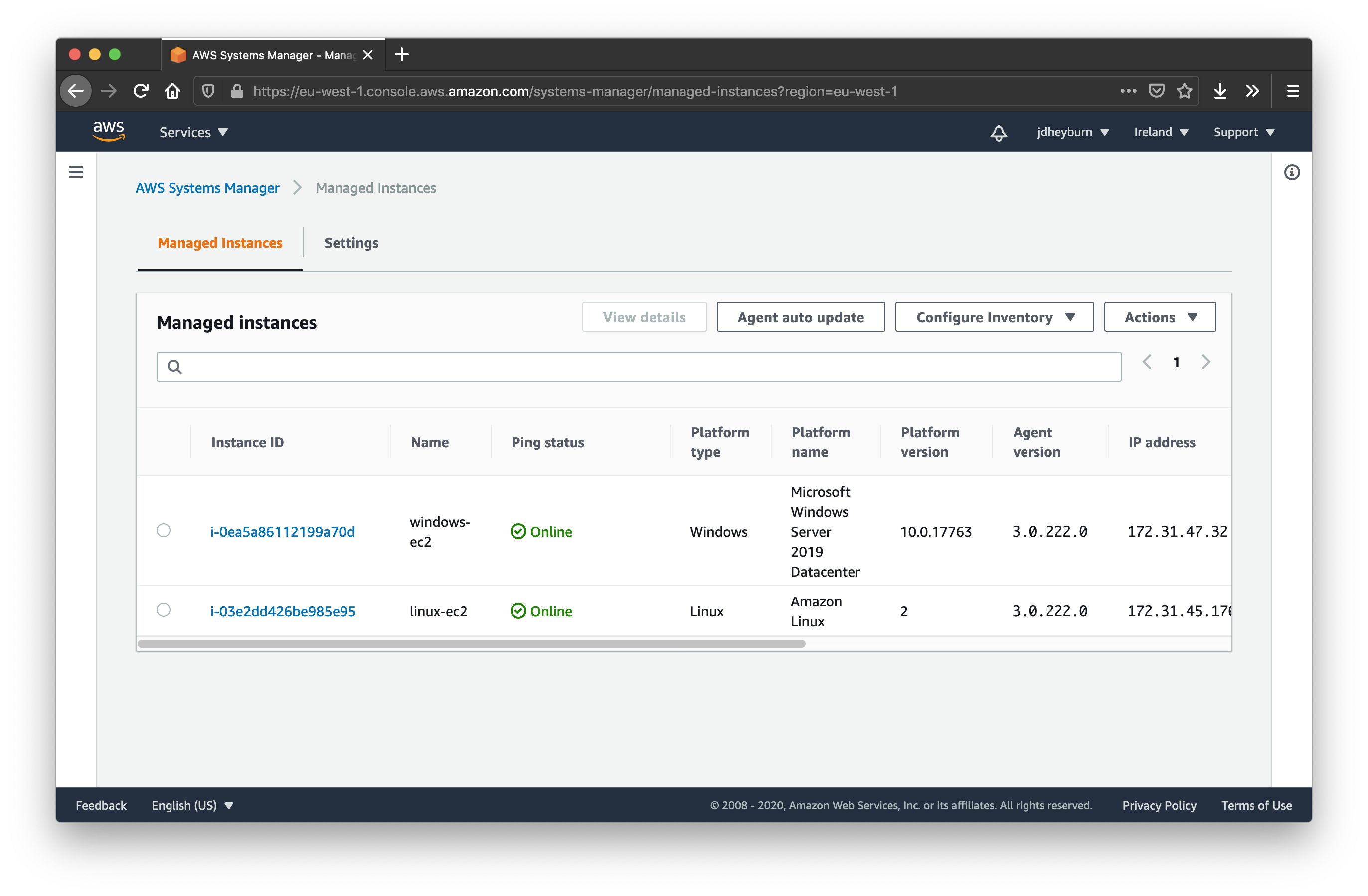



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn




Terraformでec2を使ったweb環境をつくろう Qiita



Automate Patching With Aws Systems Manager By Troy Ingram Nerd For Tech Medium



D8d5kmuys753dm



Ncqgdpgrrw5uwm
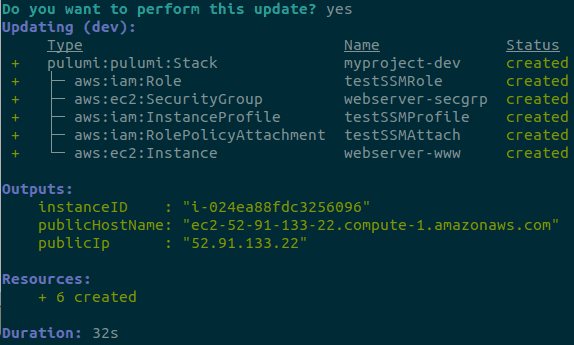



Easy Ec2 Ssm With Pulumi In Typescript Andrew Klotz



Aws Iam Role Policy Attachment Resource Produced New Value For Was Present But Now Absent Issue 119 Hashicorp Terraform Provider Aws Github



Cluster Never Comes Available After Moving To 9 0 0 Issue 757 Terraform Aws Modules Terraform Aws Eks Github




Aws Session Manager Less Infrastructure More Features Sym Blog



100 Days Of Devops Day 36 Introduction To Aws System Manager By Prashant Lakhera Medium




Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn



Github Rhythmictech Terraform Aws Atlassian Bitbucket Creates A Bitbucket Ec2 Instance And Elb
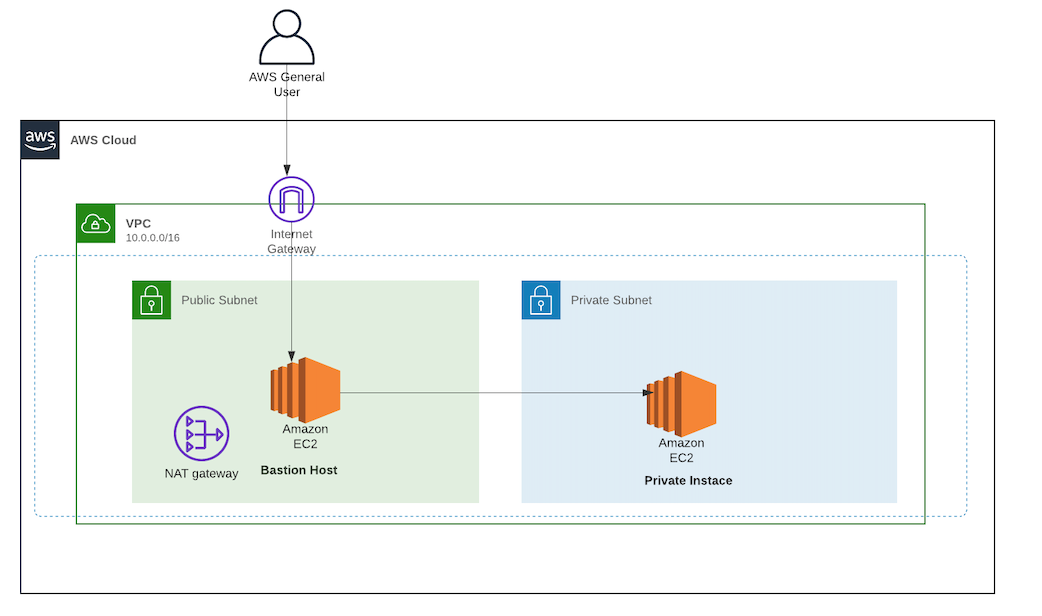



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science




Gruntwork Newsletter November By Amanda Ohmer Gruntwork



Cn3uetskaijbqm




Applying Managed Instance Policy Best Practices Aws Management Governance Blog



C Zuhmaip L Im




Stop Exposing Port 22 To The World It S Time To Rework Your Remote Access Methods Toolr Io




Elastic Beanstalk With Terraform Notes And Anecdotes



Tf Destroy Fails To Remove Aws Auth Unauthorized Terraform Aws Eks



Tf Destroy Fails To Remove Aws Auth Unauthorized Terraform Aws Eks



Login From Internet Into A Private Subnet With Session Manager By Giuseppe Borgese Medium




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh



100 Days Of Devops Day 37 Automate The Process Of Ami Creation Using System Manager Maintenance Windows By Prashant Lakhera Medium




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers




Terraform Multi Cloud Demo Part 3 Aws Infrastructure Dave S Blog



Kkqvwhgzd4taam




Terraform Multi Cloud Demo Part 3 Aws Infrastructure Dave S Blog




Kkqvwhgzd4taam



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium



Graceful Shutdown Using Simple Sytems Manager And Terraform On Aws By Paul Leclercq Tabmo Labs




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers



Tf Destroy Fails To Remove Aws Auth Unauthorized Issue 1162 Terraform Aws Modules Terraform Aws Eks Github




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers



How To Install Ssm Agent On Linux Ec2 Instances
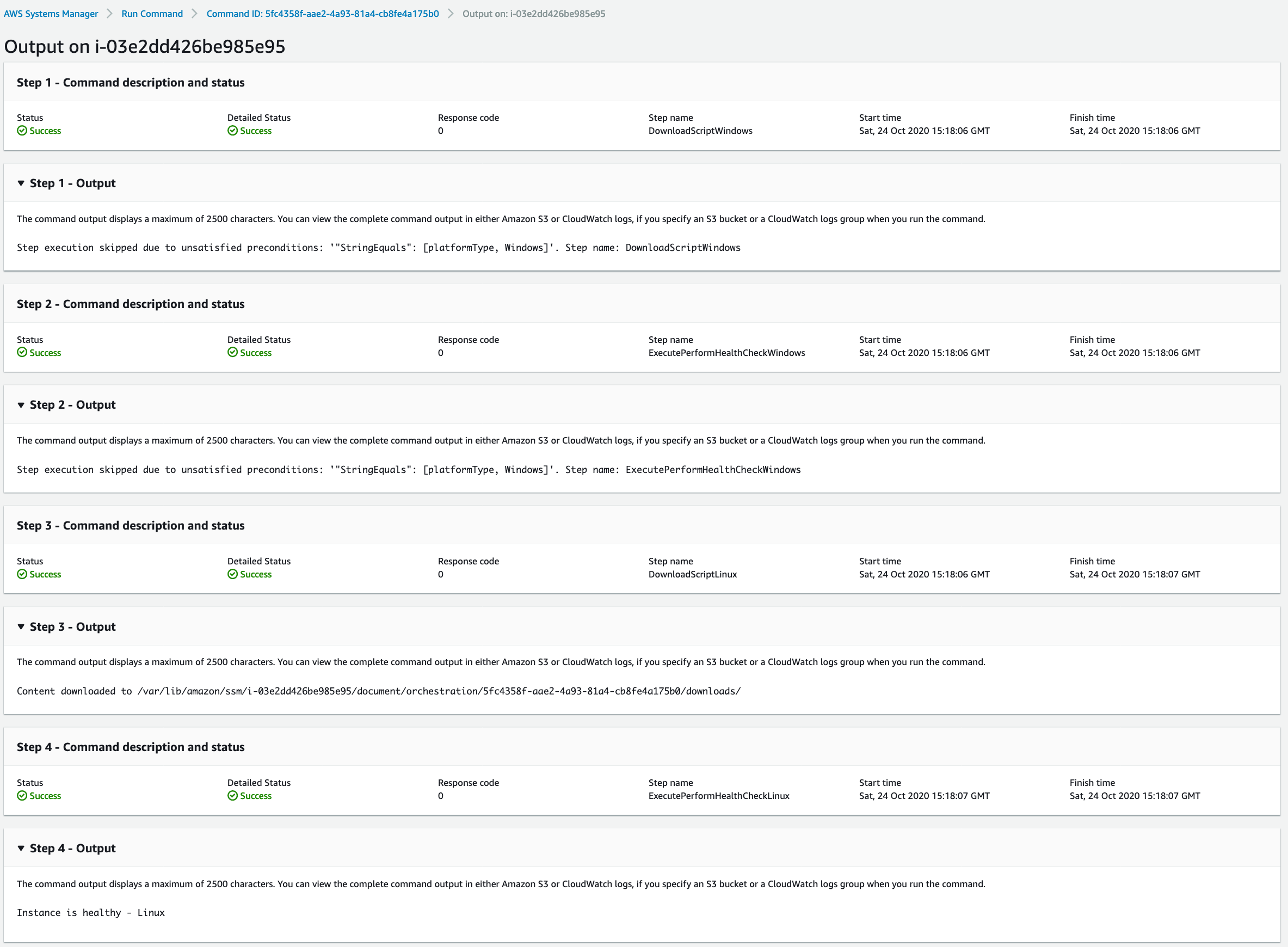



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn




Accessing Flatcar Instances Using Aws Ssm By Suraj Narwade The Platform Engineering




Sweetops Terraform For November




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers
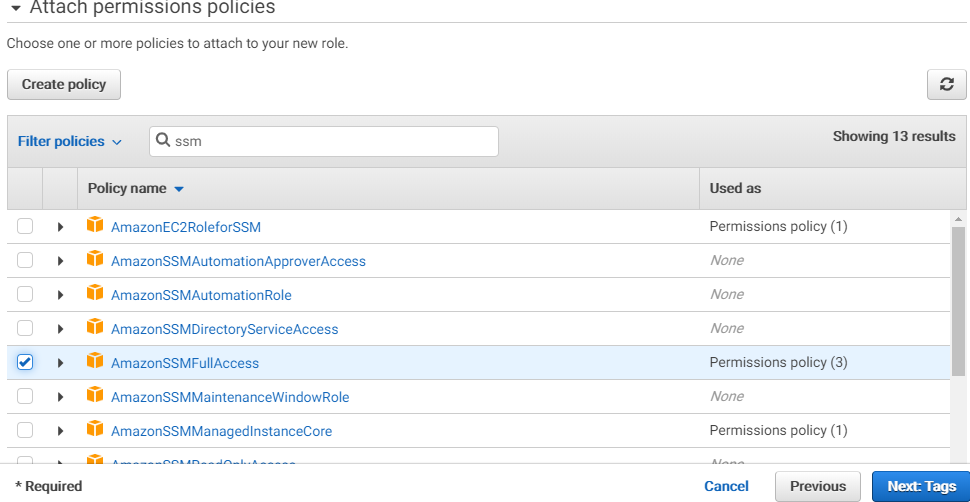



How To Install Ssm Agent On Linux Ec2 Instances



Docs Aws Amazon Com Systems Manager Latest Userguide Systems Manager Ug Pdf
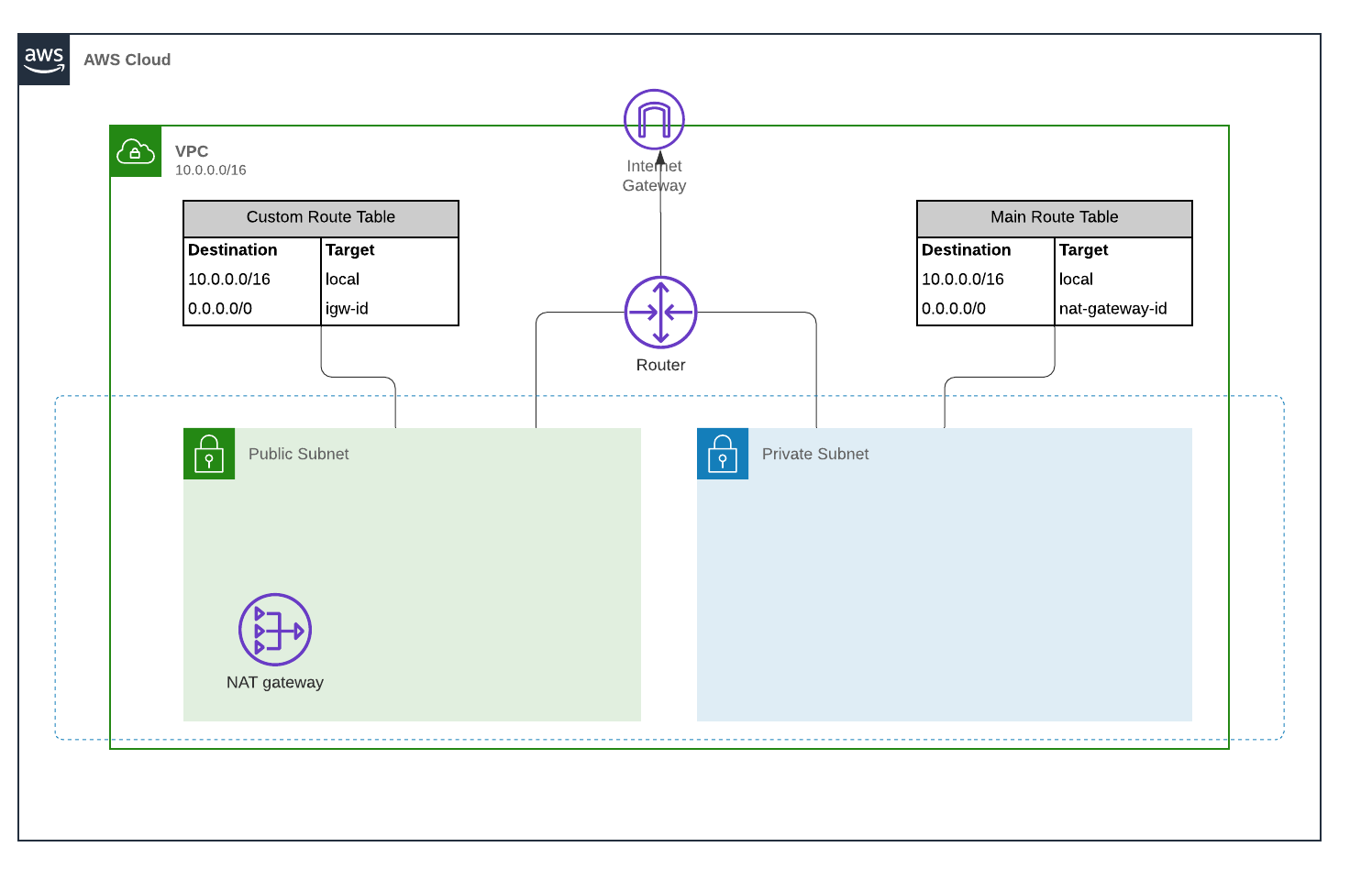



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science



Github Tieto Cem Terraform Aws Openvpn Openvpn Module




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science




Go Bastionless Access Private Ec2 Instances Using Ssm Session Manager Prasad Domala




Ed6ojaq5u2jnim




Aws Weicode




Graceful Shutdown Using Simple Sytems Manager And Terraform On Aws By Paul Leclercq Tabmo Labs




Secure Rds Access Through Ssh Tunneling Over Aws Ssm In Terraform
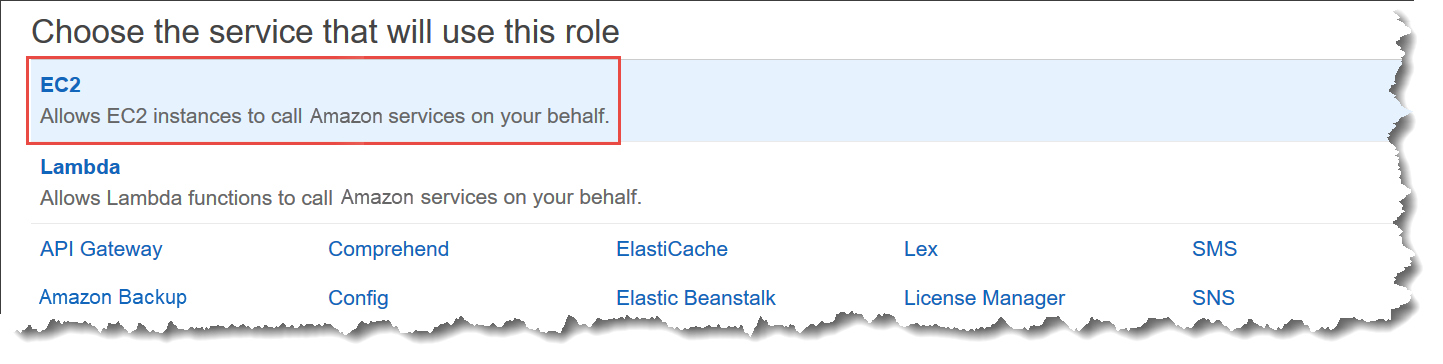



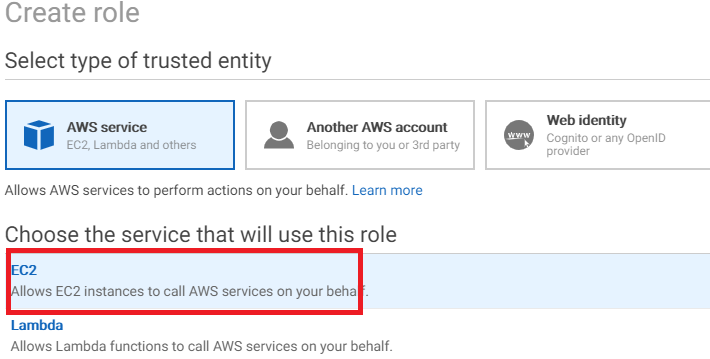
Step 4 Create An Iam Instance Profile For Systems Manager Aws Systems Manager



Error Failed To Query Available Provider Packages With Hashicorp Iam After Adding Any Iam Data Issue Hashicorp Terraform Github




Ansible Over Aws Systems Manager Sessions A Perfect Solution For High Security Environments Luktom Net



Terraform Aws Ec2 With Ssm Agent Installed




Bootstrapping A Startup On Aws With Aws Serverless And Go Devsday Ru




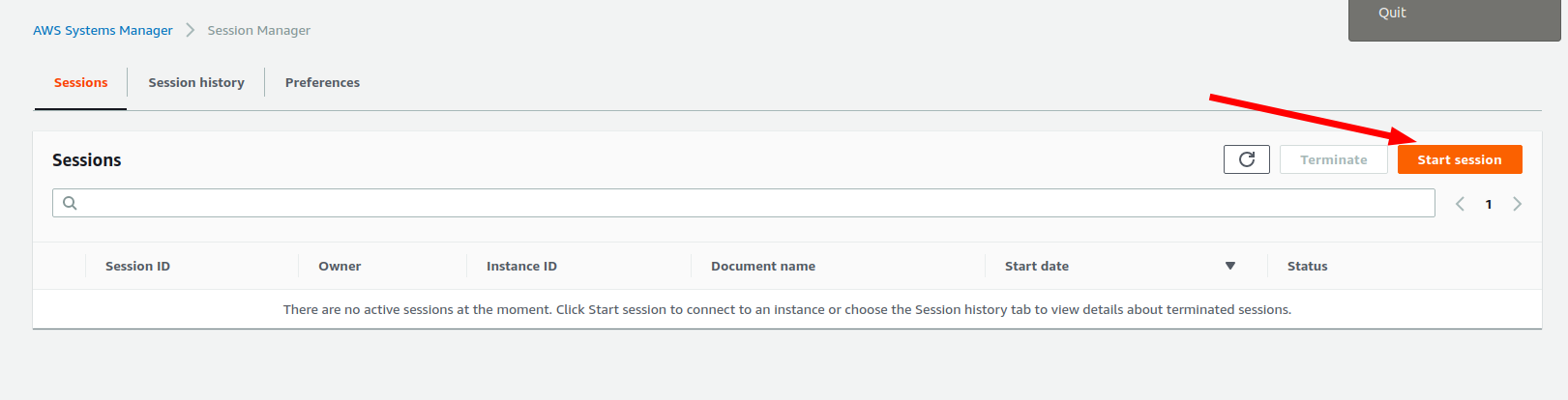
Aws System Manager Start Session An Error Occurred Targetnotconnected When Calling The Startsession Operation Instance Id Is Not Connected Stack Overflow



Xflcy1jhfpdfzm




Secure Rds Access Through Ssh Tunneling Over Aws Ssm In Terraform
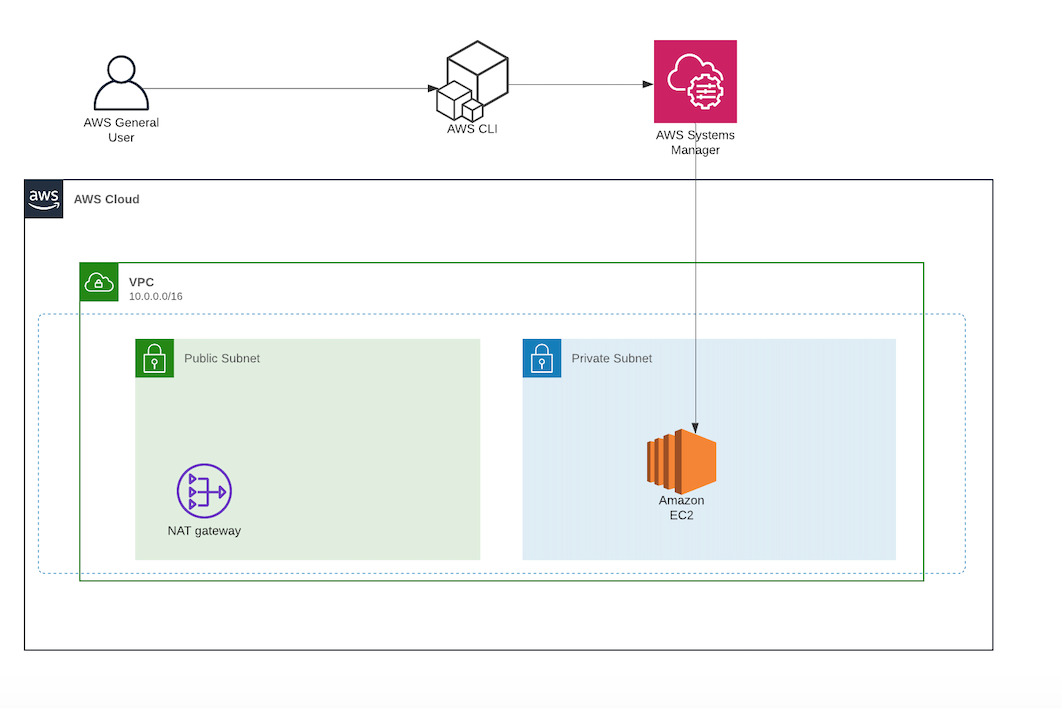



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science



Aws Iam Role Policy Attachment Using Count And List Of Polices Returns An Inconsistent Result Error If The List Order Is Changed Issue Hashicorp Terraform Provider Aws Github



0 件のコメント:
コメントを投稿